Vulnerabilities in the automation of power grids are more often on the radar screen of information and control system experts. It seems that some people are using the situation of aging infrastructures to make money with finger-pointing to the vulnerabilities of implementations of protocols like DNP3 or others. Or is it just fun to discover “holes” in the often low level secured information and communication systems?
Click HERE for a report (Electrical Grid Is Called Vulnerable to Power Shutdown) in The New York Times.
There are – in my view – two crucial issues (among other) when it comes to security measures for information exchange systems in power systems:
1. Lack in Expertise
2. Lack in Resources
There are a lot of discussions regarding aging infrastructures these days. I hope the discussions will have a real impact of securing our infrastructures, especially the electrical power system delivery systems!
Open standard protocols allow remote access to a lot of critical systems like substations or power generation sites. ENEL (Italian Power Company) operates some 400.000 Substations worldwide – some 100.000 are remotely monitored. So, 300.000 substations cannot be reached by protocols. Hundreds of protocols may be in use in the power industry. This makes it quite hard to easily break into most of the substations worldwide. With the application of standards like IEC 60870-5-104, DNP3, Modbus IP, or IEC 61850 this will change soon.
The most secure protocol is the protocol that has never implemented or used! With the acceptance of a few open protocols it is quite obvious that security measures HAVE to be put in place to secure the information exchange to some reasonable degree!
Stakeholders of power utilities have to become MORE aware of the situation of the vulnerabilities in the automation of power grids! A aging bridge may be closed – and you have to detour a bit … but a blackout of a part of the electrical power delivery system due to a lack in security may end in a crucial disaster, leaving us out of power for hours and even days.
It is worth to spend more time and resources in securing all our infrastructures – first of all the electric power delivery system. Without power: no telecommunications, no transportation, no …
The well known IEC 61850 platform “BECK IPC Chip” used in many applications provides secure communication as integrated part of the real-time operating system!
It is not sufficient to know that IEDs are available that provide a reasonable level of security: YOU MUST understand and USE such solutions!!
The architecture of the chip includes security measures:
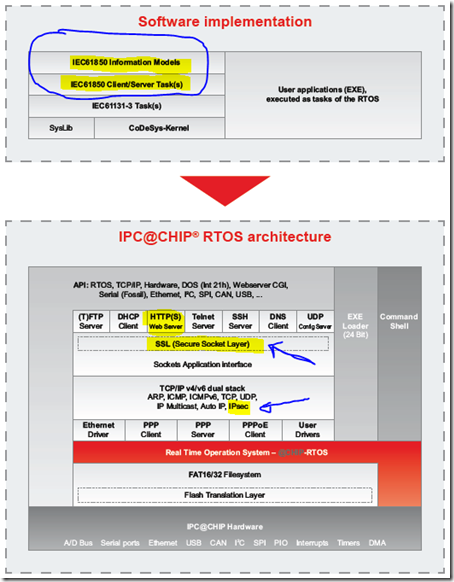
Click HERE to request more information on the security measures implemented in the RTOS and applicable for IEC 6870-5-104 and IEC 61850.
There is no need to wait for secure IEC 61850 communication! It is here.